Product Innovations Designed to be Hacked
Case Study: Raspberry Pi
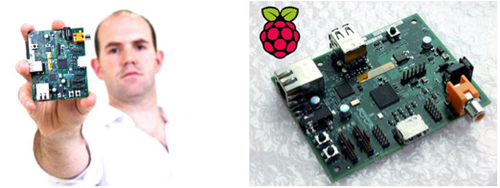
Figure 1. Raspberry Pi – the £22 computer designed to be hacked.
At the absorb and exploit end of the firm-hacker response spectrum is the non- profit UK based Raspberry Pi Foundation who introduced the Raspberry Pi computer in 2012 designed with the sole purpose of being hackable by anyone, of any age and to encourage basic computer science and programming skills in school children.
As reported in the press, the UK IT curriculum merely teaches students how to operate software packages and has been described as “demotivating and dull” by the current Education Secretary Michael Gove as [Joyce, 2012]. Students should be encouraged to learn how to modify, develop and reconfigure software for themselves as they see fit, avoiding the mysterious black box of tricks mind-set. As a consequence it is claimed that lack of coding skills is a significant barrier to future growth and holds back the UK in the digital economy age.[1]
How-to-use or operational skills do not promote a mind set or application of knowledge to make changes, improvements or modifications to existing systems themselves, but merely accept that the way they work is fixed and unchangeable. Operational skills merely allow tasks to be executed according to the pre-existing task structure through algorithms and code designed by a relatively small number of skilled software engineers within firms. These systems lock-out the possibility of further innovation or generative potential, what Zittrain refers to as potential generativity as ‘sterile appliances tethered to a network of control’ [Zittrain, 2008]. Measures put in place to fully control the user experience and maintain quality control, but also and more fervently to protect inter-firm intellectual property and appropriation of rents from within a competitive landscape; not for protecting against un-sanctioned, valued consumer acts of hacking that further-extend an artefacts’ repertoire of task execution possibilities.
One of the founding members of Raspberry Pi recently surmised what he hoped the device would achieve: ‘getting kids to engage creatively with computers: doing interesting things... it doesn’t have to be programming: it can be art [or] design, using computers in a creative way’ [Joyce, 2012]. This also begins to surmise fundamental attributes at the core of the hacker ethics. It mirrors the activities undertaken by firms in the search for new innovation (both radical and incremental) within R&D labs; the main difference being creatively exploring yet-to-be-realised technology configurations to be used in creating new products and services, rather than modifications to existing ones by its users.
Many of today’s digital devices (whether tethered to a network of control or open to modification) have a predefined set of operable functions and tasks inherent in its architecture and limited by its design. Hackers in this sense provide a means and a method to access and contribute to the generative or innovative potential held within a given technology. Whether closed by measures put in place by manufacturers or freely accessible in open systems, hackers will find ways in which to unlock the potential generativity within a technology. There are no true closed systems in the mind of the hacker, only temporary, inconvenient obstacles to overcome (firmware, software and hardware locks, encryption, copy protection, digital rights management and many others) and re- enable open or modifiable devices in the pursuit of executing further tasks with a technology whether deemed legal or otherwise.
The RasPi is an interesting market proposition, built with extremely low barriers to entry due to the £22 price tag and designed with a sole reliance on leveraging hacker communities to enable its future adoption and success. It was initially targeted at Computer Hobbyist and Enthusiast Programmers to build and develop an Open Source software base before educational institutions could begin adopting them in classrooms with a recently pre-built and rich software base.[2] The product launch strategy was intended to leverage hacker ethics, seen as passionate and playful explorers of technology, by selling ten thousand initial units to end users and hacker-innovators ahead of mainstream markets.
The computer is entirely open by design to easily permit the seeking of ways in which to execute new tasks outside those thought possible by the original architects and designers, representing an altogether different strategy to those employed by multinational technology incumbents. The RasPi foundation is trying to actually encourage and generate a culture of hackers, who inquisitively seek to control technology, not be controlled by it.
Footnotes
- ↑ Google's Eric Schmidt criticises education in the UK (http://www.bbc.co.uk/news/uk-14683133), August 2011).
- ↑ Raspberry Pi is based on a Broadcom BCM2835 system on a chip (SoC) using ARM architecture chips (commonly used in smartphones) in order to keep per unit prices as low as possible.
References
- [Joyce, 2012] ^ 1 2 Joyce, J. (2012). "Raspberry Pi computer: Can it get kids into code?". Retrieved April 3, 2012, from http://m.bbc.co.uk/news/technology-17192823.
- [Zittrain, 2008] ^ Zittrain, J. (2008). The Future of the Internet And How to Stop It New Haven & London, Yale University Press.
- [Himanen, 2001] Himanen, P. (2001). The Hacker Ethic and the Spirit of the Information Age. New York, Random House.
- [Rogers, 1995] Rogers, E. M. (1995). Diffusion of Innovations. New York, The Free Press.
- [Robson, 1999] Robson, G. (1999). "How to Become a Hacker in 2473 easy lessons." Retrieved March 20, 2012, from http://users.telenet.be/mydotcom/library/index.htm.
- [Sharma, 2012] Sharma, A. (2012). "Stuxnet - First Cyber Weapon of the World." Retrieved April 11, 2012, from http://www.symantec.com/connect/blogs/stuxnet-first-cyber- weapon-world.
- [Nappenberger, 2012] Nappenberger, B. (2012). We Are Legion: The Story of the Hacktivists.
- [IDEO, 2012] IDEO (2012). "IDEO Labs Bay Area Hack Nights." Retrieved Feb, 2012, from http://labs.ideo.com/2012/03/13/bay-area-hack-night/