Difference between revisions of "Hacker Generations and Evolution"
From Hacker Innovation: Redefinition and Examination of Outlaw Sources of Generativity for Future Product Development Strategies (2014) by Mike Pinder
Mikepinder (Talk | contribs) |
Mikepinder (Talk | contribs) |
||
| Line 1: | Line 1: | ||
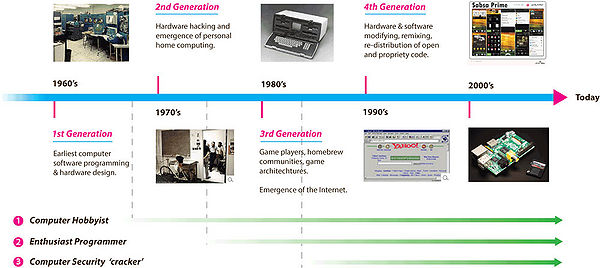
Although the extant typology of hacker activities along the illegal-to-legal dimension is useful in delineating differing types in terms of destructivity, creativity, piracy and theft, remixing of value etc., it does not take into account the evolution of different hacker types over time since their initial emergence. The typology assumes all hackers are constituent of the same generation, which is clearly not the case, given the incremental emergence of hacker generations since the 1960’s (see below). | Although the extant typology of hacker activities along the illegal-to-legal dimension is useful in delineating differing types in terms of destructivity, creativity, piracy and theft, remixing of value etc., it does not take into account the evolution of different hacker types over time since their initial emergence. The typology assumes all hackers are constituent of the same generation, which is clearly not the case, given the incremental emergence of hacker generations since the 1960’s (see below). | ||
| − | [[File:HACKER-TYPES-AND-GENERATIONS5.jpg|600px]] | + | [[File:HACKER-TYPES-AND-GENERATIONS5.jpg|600px|Emergence of hacker types and generations]] |
Revision as of 15:19, 30 August 2014
Although the extant typology of hacker activities along the illegal-to-legal dimension is useful in delineating differing types in terms of destructivity, creativity, piracy and theft, remixing of value etc., it does not take into account the evolution of different hacker types over time since their initial emergence. The typology assumes all hackers are constituent of the same generation, which is clearly not the case, given the incremental emergence of hacker generations since the 1960’s (see below).