Difference between revisions of "Hacker Generations and Evolution"
Mikepinder (Talk | contribs) (→Re-framing the extant hacker typology) |
Mikepinder (Talk | contribs) |
||
| Line 27: | Line 27: | ||
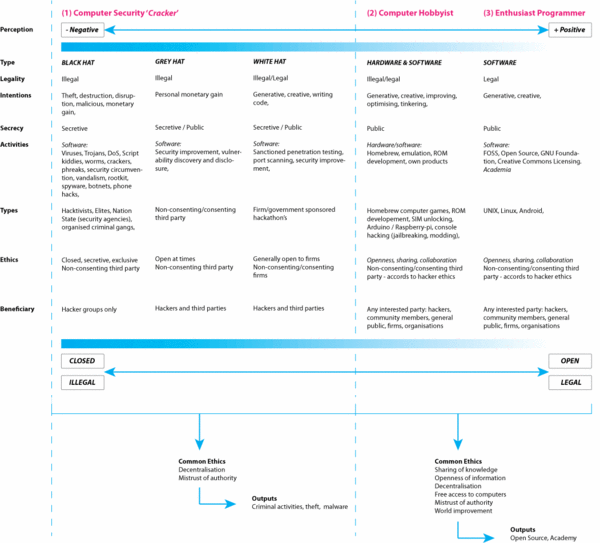
Common to all forms hacking activity along the illegal-to-legal dimension, are set of cultural beliefs and values that can shed light on motivations for the initiation of a hack in the first place. The table below shows a summary of the three main hacker activity types and the degree to which such acts may be deemed illegal by institutions or organisations claiming private intellectual property ownership over artefacts. | Common to all forms hacking activity along the illegal-to-legal dimension, are set of cultural beliefs and values that can shed light on motivations for the initiation of a hack in the first place. The table below shows a summary of the three main hacker activity types and the degree to which such acts may be deemed illegal by institutions or organisations claiming private intellectual property ownership over artefacts. | ||
| − | [[File:Typology-of-Hacker-Classes.gif|600px| | + | [[File:Typology-of-Hacker-Classes.gif|600px|border|caption]] |
==Footnotes== | ==Footnotes== | ||
Revision as of 15:31, 30 August 2014
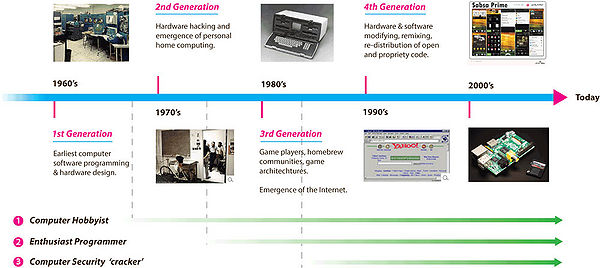
Although the extant typology of hacker activities along the illegal-to-legal dimension is useful in delineating differing types in terms of destructivity, creativity, piracy and theft, remixing of value etc., it does not take into account the evolution of different hacker types over time since their initial emergence. The typology assumes all hackers are constituent of the same generation, which is clearly not the case, given the incremental emergence of hacker generations since the 1960’s (see below).
Viewed in this way in temporal form, the Computer Security Crackers are a relatively new phenomenon; an inevitable result by those seeking to exploit and illegally profit from new emergent and openly available technologies (distributed home computing, micro-chips, networks and Internet communication technologies).
Computer Hobbyists and Enthusiast Programmers emerged long before Computer Security Crackers (despite the current focus of meaning in popular culture) and in some instances created entire industries as in the personal home computing sector.
Hackers were in fact first defined in 1984 in a book called Hackers: Heroes of the Computer Revolution, described as having evolved through several generations. An extension of this is offered below.
Contents
1st Generation Hackers (1960’s/70’s)
- Hackers involved in the earliest computer programming techniques development for technology exploration.
2nd Generation Hackers (mid 1970’s to mid 1980’s)
- Hackers in computer hardware production during the advent of Personal Computer by modifying and creating new hardware configurations (Apple, Microsoft: Jobs, Wozniak, Allen, Gates et al.).
3rd Generation Hackers (1980’s to mid 1990’s)
- Hacker-game players devoting leisure time to writing scripts and programmes for game architectures amidst the emergence of Open Source software development [Jeppessen, 2003].
4th Generation Hackers (late 1990’s to today)
- Hackers freely modifying, remixing, reconfiguring and re- distributing open and proprietary knowledge extracted from creative IP from consumer artefacts, technology, products and services facilitated by the use of information and communication technologies (ICT’s).
There is a significant need to understand the true meaning of hacking, not from a sensationalist media perspective but from its origins to uncover its motivation, goals and aims; and to find exactly what role hacking plays in today’s digitally networked society. Media coverage of hacking does nothing to promote scholarly attention to the understanding of the wider role hacking plays, and merely demotes it to illegal deviant activities involving crime, dark sub-cultures with gang mentalities. In some contexts along the illegal-to-legal dimension, these perceptions are entirely valid, but they do not hold for all types of hacking activity that can represent generativity, creativity and problem solving solutions. Only by broadening our understanding of hacking can we begin to see other forms of hacking that are not simply negative and destructive but are creative sources of potential innovation by hacker-innovators and end users alike that can be a significantly beneficial source for organisations seeking to create better experiences, products and services for their consumers.
Re-framing the extant hacker typology
Common to all forms hacking activity along the illegal-to-legal dimension, are set of cultural beliefs and values that can shed light on motivations for the initiation of a hack in the first place. The table below shows a summary of the three main hacker activity types and the degree to which such acts may be deemed illegal by institutions or organisations claiming private intellectual property ownership over artefacts.
Footnotes
References
- [Jeppessen, 2003] ^ Jeppessen, L. B. M., M. (2003). "Consumers as Co-Developers: Learning and Innovation Outside the Firm." Technology Analysis & Strategic Management 15(3).