Difference between revisions of "Hacker Ethics and Morals"
Mikepinder (Talk | contribs) (Created page with "== Common hacker ethics ==") |
Mikepinder (Talk | contribs) |
||
| (13 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
== Common hacker ethics == | == Common hacker ethics == | ||
| + | |||
| + | Within the typology of hacking explored in this paper, a common set of underlying ethical foundations is prevalent across all hacker classes. They span across all forms of hacking along the illegal-to-legal dimension, even within the aforementioned and defined Computer Security Cracker class. According to Levy [Levy, 1984], the cornerstones of the common hacker ethic are: | ||
| + | |||
| + | * Sharing of knowledge | ||
| + | * Openness of information | ||
| + | * Decentralisation | ||
| + | * Free access to computers | ||
| + | * Mistrust of authority | ||
| + | * World improvement | ||
| + | |||
| + | == Private ownership == | ||
| + | |||
| + | The concept of claimed rights to private property ownership and material goods can be traced to John Locke’s theory of property in his ''Two Treatises of Government'' [Locke, 1689]. Locke argues that property is a natural right and is derived from ones effort of labour. If you expend labour to create a good or property to benefit human society, then you have property rights over it. Adam Smith later went further to claim that private property is now an implicit given and it is the ''invisible hand'' that brings the marketplace into equilibrium through self interested gains that ultimately benefit society by keeping prices low while building incentives for a broad range of goods and services [Smith, 1776]. The economic system itself fits the interests of the capital property owners. Hackers disrupt the invisible hand by expending human labour on top of labour generated by firms, not for property ownership and monetary value exchange, but for intrinsic benefits and motivations to optimise and explore unrealised potential within a technology. The marketplace demands continuous cyclical consumption to grow, by selling employee labour effort to the employer and the employer selling resultant products and services back to the consumer. The market does not demand the best product possible in the long term for it is inferior the moment it is produced and has a limited life cycle. Hackers disrupt the cycle by disregarding private property claims and expending human labour but without private property claims. The result is intended disruption via the extension of intrinsic and planned obsolescence of consumer artefact timelines (put in place by firms to maximise returns) ultimately impacting the efficiency of consumption’s ability to drive growth in economies. Hackers pose a problem not only to firms competing on the basis of the creation of value through private property but also to economic growth as a whole. | ||
| + | |||
| + | Amidst popular misconceptions about actual hacker (not ''cracker'') activities and in order to understand the emergence of the hacker mentality as a whole, it is vital to understand hacker attitudes and culture mind set towards ownership and private property, as they span-across and underpin a broad range of external user innovation activities. Some of these can be traced back to abstractions to the idea of private ownership discussed in the book: ''A Hacker Manifesto'' [Wark, 2004]. | ||
| + | |||
| + | Key to the hacker mentality is the idea of private ownership of information. It is claimed that “''information wants to be free but everywhere it is in chains'',” though the use of IP regimes, patents and copyright that permit the legal rights and means of extracting value by its owners.<ref>Wark, McKenzie. “Information Wants to be Free (But is Everywhere in Chains).” Cultural Studies 20.2-3 (2006).</ref> Referring to Marx, Wark discusses modes of production, distribution and consumption that create deprivation in order to maintain unequal social relations through the application of economics [Marx, 1848]. The hacker ethic at an extreme and abstract level is refuting any ownership claims to private property over and above nature itself. | ||
| + | |||
| + | In the 1970’s an electronics engineer called John Draper discovered that a free toy whistle packaged with popular children’s cereal Cap’n Crunch could easily be modified to reproduce the 2600-hertz frequency used by AT&T for long distance telephone calling. This allowed anyone with hacked whistle to place free anonymous long distance phone calls anywhere in the World using untraceable toll-free-800 calls. Draper went on to build a phreaking tool called the blue box and featured in Esquire magazine in 1971.<ref>Rosenbaum, R. “Secrets of the Little Blue Box,” Esquire Magazine, October 1971, retrieved November 2012, available at: http://www.historyofphonephreaking.org/docs/rosenbaum1971.pdf</ref> Inspired by the article, Steve Jobs and Steve Wozniak entered into production of digital blue boxes, raising $6000 to help start up Apple Computers. Blue box devices allowed teenagers (for a hundred dollars) to gain total control of hundreds of billions of dollars of international telephony infrastructure, exchanges, routing computers and satellites. For hackers this meant something much more than simply making free calls around the World. It stirred-up a debate about publically tax-funded projects such as ARPANET (later to become the Internet) and public telephone infrastructures belonging to the people who funded them. In this way hackers felt that such systems were not a proprietary ''owned'' asset and should be free for exploration, learning, improvement and innovation of any kind or source provided you were a legitimate expert. Governments and legal systems were in effect ‘legitimately’ abstracting ownership away from the people whilst conflicting with rising hacker classes, culture and ethics. Blue boxes were the means to emancipate the technologies and allow for unrestricted systems exploration and learning to take place. Draper stated his intentions were not simply to make free calls but ‘...to show Ma Bell how good I am. I don't want to screw her, I want to work for her. I want to do good for her. I want to help her get rid of her flaws and become perfect. That's my number-one goal in life now’ [Rosenbaum, 1971]. Underlying motivations for hacking are again, not about theft of intellectual, but about unrestricted generative exploration of a given technology in order to improve it for the benefit of all. | ||
| + | |||
| + | Further understanding of the idea of abstraction of nature can be found in the process of permanently taking and claiming ownership of groundwater from a natural source, known as ''abstraction of water''. Abstraction in this sense refers to claiming and taking private ownership of a naturally occurring resource; ''abstracting'' it away from its naturally created, un-ownable state, to private ownership as a valuable and tradable market commodity, simply by claiming ownership in the act of assuming claimant rights over it. For hackers and the hacker ethic, information is abstracted in this same way. Merely claiming intellectual property or ownership, through legal systems, intellectual property regimes or otherwise do not give adequate justification for the abstraction to occur in the first place, and it is the activities of hackers who restore ownership to its freely occurring, natural ownership free state. The abstraction and privatisation of property is seen as an institutionalised legal hack over generations of claimants, from peasants to farmers to workers to capitalists to vectoralists; the progression of ownership from land (pastoralist) to capital (capitalist) to information (vectoralist).<ref>Vectoralists control the vectors of information, IP, patents, trademarks; means of producing value by means of war like strategies of communication, command and control.</ref> | ||
| + | |||
| + | Artefact ownership and private property are seen as an abstraction of natural and physical spaces labelled as real estate and patent portfolios. The abstraction of one’s labour time needed to convert its produce into surplus value via the paid wage. In the information age, the hack is an abstraction of labour time into an information surplus and to convert this surplus value into revenue, products and services to be bought and sold. | ||
| + | |||
| + | From a critical lens, in the material world economics is used to allocate limited resources to unlimited demands, moderated by scarcity of commodities and resources in order to maintain unequal social relations. However in the digital age, information is not scarce but entirely abundant and free to exchange without incurring significant transaction costs. It can be sent, received and duplicated at negligible cost. Furthermore (and more critically), information once free from ownership is ''nonrivalrous''. Its possession does not create the same economic scarcity, permitting freedom from true private and exclusive ownership. Hackers seek to make all information ownership-free in this regard through the organisation of free-collective expression and to serve the people directly, rather than by merely serving the ruling vectoralist classes. For hackers information cannot and should not be commodified as a resource. | ||
| + | |||
| + | The hacker in essence is someone engaged in a struggle against the expropriation of value by the ''vectoralist'' class via the control and extraction of surplus from the productive classes.<ref>Other ruling classes: pastorialists who control extracting value from land and capitalists who control means of production and distribution of value.</ref> The hacker class is a producer of new abstractions within a world of abstractions to serve the people directly and independent of the ruling classes. The more information is free, the more the ruling classes depend upon the enforcement of law to secure its rent, profit and margin; making law and legal frameworks the key instrument in preserving power. | ||
| + | |||
| + | Hackers fundamentally seek to ''free'' knowledge from imposed economic scarcity by the ruling classes, to the point where “the free production of knowledge itself becomes the knowledge of free producers” (Wark 2004, p. 40). Hackers simply aim to place the means of producing and creating value in the hands of productive classes. By the act of hacking, scarcity is overcome (or circumvented by other means) and releases the surplus of productivity, owned by the ruling classes, back into the hands of the producers. At this instant, the working classes no longer have to re-consume their own abstracted labour efforts. Ruling classes attempting to commodify the resultant generativity of a hack (as it represents a further market opportunity to extract margins from a scarce resource), but militarised hacker ethics coordinated and organised by digital technologies presents a challenge for would-be appropriators as the underlying characteristics of the technologies themselves built, developed and sold by the economic systems would fundamentally challenge any firm’s ability to achieve value generation in this way.<ref>With reference to Computer Security Cracking group Anonymous and recent backlash attacks in response to institutions attempting to impose barriers against the public release and sharing of information and knowledge.</ref> <ref>See film documentary ‘We Are Legion, The Story of the Hacktivists’ (2012) for examples of hacker backlashes against the firm.</ref> | ||
| + | |||
| + | == UK Freedom of Information Act 2000 == | ||
| + | |||
| + | The UK Freedom of Information Act (FOIA) is designed with hacker ethics in mind, defined to ensure that governmental organisations cannot be secretive about public information and that ‘everyone has the right to request information held by public sector organisations’ [Parliament, 2000]. Under this act any person can ask for access to any public body for all the information they have on a subject they choose. | ||
| + | |||
| + | Black hat hackers have strived for such ideals for decades taking and stealing public and private information through any means necessary, claiming that information wants to be free from ownership by anyone. Hackers of all classes in this sense have been liberators of information being held hostage by agents demanding money for its release. WikiLeaks continually operates at the sharp end of this idea, by releasing highly confidential, secret and classified information into the public domain, an extreme boundary free version of the UK FOIA. It operates as a highly public black hat hacking outlet, agent and public distributor [Assange, 2012]. The UK FOIA has broken down the cartel of information trading and ownership from within the political elites to the press and media. Anyone can request information directly, bypassing all ownership agents, (and the need for bribes and back-handers along the way) with the power of the law supporting them. It allows for legalised hacker ends without the need for illegal hacker means. It is a strong sign that hacker ethics are present in some forms within the echelons of the vectoralist classes and encouraging a culture of openness and freeing information of property ownership and control right the way through society. | ||
| + | |||
| + | == Gift economies == | ||
| + | |||
| + | Anthropologists have only ever found gift economies (defined as instances where relationships of obligation and reciprocity emerge), in societies where material abundance is found. This begins to explain the gift culture found various hacker communities such as the Free Software communities within the abundance of digital information flourishing in freely available, ownerless open code form. | ||
| + | |||
| + | For hackers, claims to exclusive private ownership of data are theft; theft from nature stemming right back from the initial abstraction claims of land ownership by pastoralist classes. Hacking as a gift, as in Free Software, returns the concept of ownership back to nature, the environment and the commons by de- commoditising private property claims of information by those seeking to control it as a scarce resource in which to extract rents. | ||
| + | |||
| + | [[File:Underlying-Hacker-Ethics.gif|300px|border]] | ||
| + | |||
| + | '''Figure 1. Underlying hacker ethics applicable to a range of other hacker activities outside computing and code development.''' | ||
| + | |||
| + | Underpinning Enthusiast Programmer and Computer Hobbyist hackers are a strong set of ethics (openness, sharing, collaboration) embedded in a sub-culture that originated within academic circles at MIT, University of Berkley, Carnegie Mellon University and the Homebrew Computer Club (see Figure 1 above). Here hacking was seen as an act involving skill, a sense of playfulness and creative and lateral thinking to push the boundaries and limits of current technology and knowledge. These original academic enthusiast programmers formed the foundations for the free software movement, GNU manifesto and the Open Source software innovation models today.<ref>It is vital to distinguish between Free Software and Open Source. Free Software (GNU Project) refers to the freedom to share code with one’s neighbor for any usage or purpose as a moral argument whilst Open Source provides a business economic argument through code usage being beneficial to the firm but based on strict licensing agreements. Eric Raymond argues that the Free Software term was too wide and ambiguous for business to embrace and instead promoted the Open Source term to be less threatening to existing business models as many software features and designs were appropriated from Microsoft and Unix vendors (HP, IBM & Sun).</ref> | ||
| + | |||
| + | == Hacker dependence == | ||
| + | |||
| + | Founder of the GNU operating system (meaning GNU’s not Unix) and General Public Licensing agreement, Richard Stallman, goes as far as to claim that capitalism itself is ‘based upon the exploitation of the [open] scientific community’ by openly exploiting scientific knowledge advances and allows firms to generate competitive advantage over competitors seeking to generate similar value.<ref>GNU General Public License v3.0 available at: http://www.gnu.org/copyleft/gpl.html.</ref> By extension, the ruling classes also depend upon advances hackers produce in generating competitive advantage for their enterprises (development of the World Wide Web, Linux, Open Source Software).<ref>Reflected in recent firm policy and attitude changes towards Open Source by incumbents such as IBM and Microsoft who now invest and contribute widely into openly developed code.</ref> Hackers generally seek what is systemically contradictory to firms: open, public expansion of all the vectors of communication, culture and knowledge around the globe. | ||
| + | |||
| + | ==Differences between consumer fans and hackers== | ||
| + | |||
| + | Fans are a group of consumers who desire to worship an artefact created by someone else; a new tablet computer or latest smartphone for example. The key difference between fans and hackers is that fans have no desire to create something new, reconfigure or remix a product in some way to make improvements or solve as yet unmet needs or demands. Marketing and advertising has long sought to make consumers unilaterally loyal fans of a particular brand product or service by engaging in the consumer’s aspirational desires through making imaginative associations between actual products and what it is people dream of. However hackers are rather different from fans as they are disruptive entities, sceptical of dominant commercial brands with a desire to create something alternative to the mainstream that fans may typically celebrate. | ||
| + | |||
| + | Lego (the Danish plastic toy brick maker) found that a consumer hacker innovator had broken-into and reprogrammed the software designed for their range of children’s robots toys called Mindstorms NXT. Instead of attempting to prosecute hackers in protection of non-sanctioned usage of proprietary intellectual property and infringement of End User License Agreements (EULA’s), Lego took a non-aggressive stance allowing the hacks to flourish by open-sourcing (releasing to the commons) the NXT firmware along with hardware component schematics and even establishing the LEGO® MINDSTORMS® Developer Program to further promote its product hacking.<ref>A book titled: LEGO MINDSTORMS NXT Hacker's Guide by Dave Prochnow with the aim of encouraging further exploration of the capabilities of the robotics system for all hacker ages.</ref> In so doing, Lego largely embraced end-user hacker innovation and sought ways in which externally created value could be used in order to further enhance the brand image and future innovation strategy, ultimately leading to the sale of more products to consumers that it had not initially targeted in its marketing research. This is a good example of how firm and hacker desires and outcomes can be brought into alignment to allow for mutually beneficial collaboration and to take advantage of each other’s motivations to innovate towards the same ends. | ||
| + | |||
| + | Hackers and firms are in a fundamental epistemological battle of opposing extremes. One the one hand, the necessity for private ownership of property to allow for the appropriation of rents from effort, and on the other, a desire for free and open access to information and property for the benefit of society as a whole. | ||
| + | All forms of hacking along the illegal-to-legal dimension demonstrate the application of a common set of underlying ethics that attempt to expand the vectors of communication, culture and knowledge around the World for the betterment of society via the generation and use of ownerless information and resources. | ||
| + | Not just restricted to digital programming and software technology development, but also applied to other contexts and domains in the networked, information economy, these ethics form the central belief structure of large groups of consumers who are prepared to partake and contribute time, effort and energy for consumption in the public collective domain. | ||
| + | |||
| + | In this way hacker ethics are a common set of ideological beliefs and values about the relationship between humans and surrounding natural environment that can easily fall in conflict with the commercial interests of firms and the economic legal systems that support the institutions. However if dynamic interconnected relationships can be fully understood, carefully managed and fostered, then internal R&D combined with hacker innovation communities should be closer aligned to make innovation less uncertain in driving market relevant outputs. Potential outcomes of adopting a sympathetic attitude and organisational culture towards hacker ethics in consumer product design may include a higher capacity to facilitate and benefit from unanticipated changes to artefacts through unfiltered contributions from broadly skilled and distributed hacker innovation communities. | ||
| + | |||
| + | True hackers essentially want to ''learn to control digital devices'', rather than ''be controlled by them''. They want to create and improve, not simply nihilistically destroy as may be commonly assumed. Market valuable knowledge and data is constantly being generated and is freely available to be exploited by suitably motivated firms to inform the creation of future product generations and understand unmet needs. | ||
| + | |||
| + | In the next chapter, the dynamics of hacks carried out on technological artefacts will be explored in more detail to understand how modular architectures are affected and innovated upon as a complementary resource for firms. | ||
| + | |||
| + | NEXT: '''Chapter 4.1''' - [[Hackers, Problem Solving and Innovation]] | ||
| + | |||
| + | <disqus></disqus> | ||
| + | |||
| + | |||
| + | [[File:hackers-and-innovation-epub-pdf-book111.png|250px|link=http://www.mikepinder.co.uk/store/e-books/hackers-innovation-redefinition-examination-outlaw-sources-generativity-future-product-development-strategies/ ]] | ||
| + | |||
| + | <big>'''''Purchase E-Book (ePub & PDF) Version'''''</big> | ||
| + | |||
| + | You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader. | ||
| + | |||
| + | [[File:add-basket-version.png|link=http://www.mikepinder.co.uk/store/e-books/hackers-innovation-redefinition-examination-outlaw-sources-generativity-future-product-development-strategies/]] | ||
| + | |||
| + | |||
| + | ==Footnotes== | ||
| + | <references/> | ||
| + | |||
| + | ==References== | ||
| + | <HarvardReferences> | ||
| + | * [*Levy, 1984] Levy, S. (1984). Hackers: Heroes of the Computer Revolution, Penguin. | ||
| + | * [*Locke, 1689] Locke, J. (1689). Two Treatises of Government: In the Former, The False Principles and Foundation of Sir Robert Filmer, And His Followers, are Detected and Overthrown. The Latter is an Essay concerning The True Original, Extent, and End of Civil-Government. | ||
| + | * [*Smith, 1776] Smith, A. (1776). An Inquiry into the Nature and Causes of the Wealth of Nations. London. | ||
| + | * [*Wark, 2004] Wark, M. (2004). A Hacker Manifesto. Cambridge, Harvard College. | ||
| + | * [*Marx, 1848] Marx, K. (1848) The Communist Manifesto. | ||
| + | * [*Rosenbaum, 1971] Rosenbaum, R. (1971). Secrets of the Little Blue Box. Esquire: 117-226. | ||
| + | * [*Parliament, 2000] Parliament, U. (2000). Freedom of Information Act. ch3600s08a. 2000 c. 36. | ||
| + | * [*Assange, 2012] Assange, J. (2012). "WikiLeaks." Retrieved Sep, 2012, from http://www.wikileaks.org/. | ||
| + | |||
| + | |||
| + | |||
| + | </HarvardReferences> | ||
Latest revision as of 10:40, 25 April 2016
Contents
Common hacker ethics
Within the typology of hacking explored in this paper, a common set of underlying ethical foundations is prevalent across all hacker classes. They span across all forms of hacking along the illegal-to-legal dimension, even within the aforementioned and defined Computer Security Cracker class. According to Levy [Levy, 1984], the cornerstones of the common hacker ethic are:
- Sharing of knowledge
- Openness of information
- Decentralisation
- Free access to computers
- Mistrust of authority
- World improvement
Private ownership
The concept of claimed rights to private property ownership and material goods can be traced to John Locke’s theory of property in his Two Treatises of Government [Locke, 1689]. Locke argues that property is a natural right and is derived from ones effort of labour. If you expend labour to create a good or property to benefit human society, then you have property rights over it. Adam Smith later went further to claim that private property is now an implicit given and it is the invisible hand that brings the marketplace into equilibrium through self interested gains that ultimately benefit society by keeping prices low while building incentives for a broad range of goods and services [Smith, 1776]. The economic system itself fits the interests of the capital property owners. Hackers disrupt the invisible hand by expending human labour on top of labour generated by firms, not for property ownership and monetary value exchange, but for intrinsic benefits and motivations to optimise and explore unrealised potential within a technology. The marketplace demands continuous cyclical consumption to grow, by selling employee labour effort to the employer and the employer selling resultant products and services back to the consumer. The market does not demand the best product possible in the long term for it is inferior the moment it is produced and has a limited life cycle. Hackers disrupt the cycle by disregarding private property claims and expending human labour but without private property claims. The result is intended disruption via the extension of intrinsic and planned obsolescence of consumer artefact timelines (put in place by firms to maximise returns) ultimately impacting the efficiency of consumption’s ability to drive growth in economies. Hackers pose a problem not only to firms competing on the basis of the creation of value through private property but also to economic growth as a whole.
Amidst popular misconceptions about actual hacker (not cracker) activities and in order to understand the emergence of the hacker mentality as a whole, it is vital to understand hacker attitudes and culture mind set towards ownership and private property, as they span-across and underpin a broad range of external user innovation activities. Some of these can be traced back to abstractions to the idea of private ownership discussed in the book: A Hacker Manifesto [Wark, 2004].
Key to the hacker mentality is the idea of private ownership of information. It is claimed that “information wants to be free but everywhere it is in chains,” though the use of IP regimes, patents and copyright that permit the legal rights and means of extracting value by its owners.[1] Referring to Marx, Wark discusses modes of production, distribution and consumption that create deprivation in order to maintain unequal social relations through the application of economics [Marx, 1848]. The hacker ethic at an extreme and abstract level is refuting any ownership claims to private property over and above nature itself.
In the 1970’s an electronics engineer called John Draper discovered that a free toy whistle packaged with popular children’s cereal Cap’n Crunch could easily be modified to reproduce the 2600-hertz frequency used by AT&T for long distance telephone calling. This allowed anyone with hacked whistle to place free anonymous long distance phone calls anywhere in the World using untraceable toll-free-800 calls. Draper went on to build a phreaking tool called the blue box and featured in Esquire magazine in 1971.[2] Inspired by the article, Steve Jobs and Steve Wozniak entered into production of digital blue boxes, raising $6000 to help start up Apple Computers. Blue box devices allowed teenagers (for a hundred dollars) to gain total control of hundreds of billions of dollars of international telephony infrastructure, exchanges, routing computers and satellites. For hackers this meant something much more than simply making free calls around the World. It stirred-up a debate about publically tax-funded projects such as ARPANET (later to become the Internet) and public telephone infrastructures belonging to the people who funded them. In this way hackers felt that such systems were not a proprietary owned asset and should be free for exploration, learning, improvement and innovation of any kind or source provided you were a legitimate expert. Governments and legal systems were in effect ‘legitimately’ abstracting ownership away from the people whilst conflicting with rising hacker classes, culture and ethics. Blue boxes were the means to emancipate the technologies and allow for unrestricted systems exploration and learning to take place. Draper stated his intentions were not simply to make free calls but ‘...to show Ma Bell how good I am. I don't want to screw her, I want to work for her. I want to do good for her. I want to help her get rid of her flaws and become perfect. That's my number-one goal in life now’ [Rosenbaum, 1971]. Underlying motivations for hacking are again, not about theft of intellectual, but about unrestricted generative exploration of a given technology in order to improve it for the benefit of all.
Further understanding of the idea of abstraction of nature can be found in the process of permanently taking and claiming ownership of groundwater from a natural source, known as abstraction of water. Abstraction in this sense refers to claiming and taking private ownership of a naturally occurring resource; abstracting it away from its naturally created, un-ownable state, to private ownership as a valuable and tradable market commodity, simply by claiming ownership in the act of assuming claimant rights over it. For hackers and the hacker ethic, information is abstracted in this same way. Merely claiming intellectual property or ownership, through legal systems, intellectual property regimes or otherwise do not give adequate justification for the abstraction to occur in the first place, and it is the activities of hackers who restore ownership to its freely occurring, natural ownership free state. The abstraction and privatisation of property is seen as an institutionalised legal hack over generations of claimants, from peasants to farmers to workers to capitalists to vectoralists; the progression of ownership from land (pastoralist) to capital (capitalist) to information (vectoralist).[3]
Artefact ownership and private property are seen as an abstraction of natural and physical spaces labelled as real estate and patent portfolios. The abstraction of one’s labour time needed to convert its produce into surplus value via the paid wage. In the information age, the hack is an abstraction of labour time into an information surplus and to convert this surplus value into revenue, products and services to be bought and sold.
From a critical lens, in the material world economics is used to allocate limited resources to unlimited demands, moderated by scarcity of commodities and resources in order to maintain unequal social relations. However in the digital age, information is not scarce but entirely abundant and free to exchange without incurring significant transaction costs. It can be sent, received and duplicated at negligible cost. Furthermore (and more critically), information once free from ownership is nonrivalrous. Its possession does not create the same economic scarcity, permitting freedom from true private and exclusive ownership. Hackers seek to make all information ownership-free in this regard through the organisation of free-collective expression and to serve the people directly, rather than by merely serving the ruling vectoralist classes. For hackers information cannot and should not be commodified as a resource.
The hacker in essence is someone engaged in a struggle against the expropriation of value by the vectoralist class via the control and extraction of surplus from the productive classes.[4] The hacker class is a producer of new abstractions within a world of abstractions to serve the people directly and independent of the ruling classes. The more information is free, the more the ruling classes depend upon the enforcement of law to secure its rent, profit and margin; making law and legal frameworks the key instrument in preserving power.
Hackers fundamentally seek to free knowledge from imposed economic scarcity by the ruling classes, to the point where “the free production of knowledge itself becomes the knowledge of free producers” (Wark 2004, p. 40). Hackers simply aim to place the means of producing and creating value in the hands of productive classes. By the act of hacking, scarcity is overcome (or circumvented by other means) and releases the surplus of productivity, owned by the ruling classes, back into the hands of the producers. At this instant, the working classes no longer have to re-consume their own abstracted labour efforts. Ruling classes attempting to commodify the resultant generativity of a hack (as it represents a further market opportunity to extract margins from a scarce resource), but militarised hacker ethics coordinated and organised by digital technologies presents a challenge for would-be appropriators as the underlying characteristics of the technologies themselves built, developed and sold by the economic systems would fundamentally challenge any firm’s ability to achieve value generation in this way.[5] [6]
UK Freedom of Information Act 2000
The UK Freedom of Information Act (FOIA) is designed with hacker ethics in mind, defined to ensure that governmental organisations cannot be secretive about public information and that ‘everyone has the right to request information held by public sector organisations’ [Parliament, 2000]. Under this act any person can ask for access to any public body for all the information they have on a subject they choose.
Black hat hackers have strived for such ideals for decades taking and stealing public and private information through any means necessary, claiming that information wants to be free from ownership by anyone. Hackers of all classes in this sense have been liberators of information being held hostage by agents demanding money for its release. WikiLeaks continually operates at the sharp end of this idea, by releasing highly confidential, secret and classified information into the public domain, an extreme boundary free version of the UK FOIA. It operates as a highly public black hat hacking outlet, agent and public distributor [Assange, 2012]. The UK FOIA has broken down the cartel of information trading and ownership from within the political elites to the press and media. Anyone can request information directly, bypassing all ownership agents, (and the need for bribes and back-handers along the way) with the power of the law supporting them. It allows for legalised hacker ends without the need for illegal hacker means. It is a strong sign that hacker ethics are present in some forms within the echelons of the vectoralist classes and encouraging a culture of openness and freeing information of property ownership and control right the way through society.
Gift economies
Anthropologists have only ever found gift economies (defined as instances where relationships of obligation and reciprocity emerge), in societies where material abundance is found. This begins to explain the gift culture found various hacker communities such as the Free Software communities within the abundance of digital information flourishing in freely available, ownerless open code form.
For hackers, claims to exclusive private ownership of data are theft; theft from nature stemming right back from the initial abstraction claims of land ownership by pastoralist classes. Hacking as a gift, as in Free Software, returns the concept of ownership back to nature, the environment and the commons by de- commoditising private property claims of information by those seeking to control it as a scarce resource in which to extract rents.
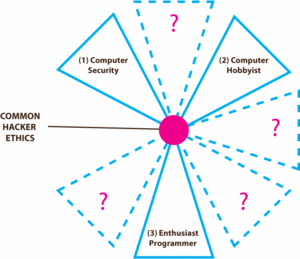
Figure 1. Underlying hacker ethics applicable to a range of other hacker activities outside computing and code development.
Underpinning Enthusiast Programmer and Computer Hobbyist hackers are a strong set of ethics (openness, sharing, collaboration) embedded in a sub-culture that originated within academic circles at MIT, University of Berkley, Carnegie Mellon University and the Homebrew Computer Club (see Figure 1 above). Here hacking was seen as an act involving skill, a sense of playfulness and creative and lateral thinking to push the boundaries and limits of current technology and knowledge. These original academic enthusiast programmers formed the foundations for the free software movement, GNU manifesto and the Open Source software innovation models today.[7]
Hacker dependence
Founder of the GNU operating system (meaning GNU’s not Unix) and General Public Licensing agreement, Richard Stallman, goes as far as to claim that capitalism itself is ‘based upon the exploitation of the [open] scientific community’ by openly exploiting scientific knowledge advances and allows firms to generate competitive advantage over competitors seeking to generate similar value.[8] By extension, the ruling classes also depend upon advances hackers produce in generating competitive advantage for their enterprises (development of the World Wide Web, Linux, Open Source Software).[9] Hackers generally seek what is systemically contradictory to firms: open, public expansion of all the vectors of communication, culture and knowledge around the globe.
Differences between consumer fans and hackers
Fans are a group of consumers who desire to worship an artefact created by someone else; a new tablet computer or latest smartphone for example. The key difference between fans and hackers is that fans have no desire to create something new, reconfigure or remix a product in some way to make improvements or solve as yet unmet needs or demands. Marketing and advertising has long sought to make consumers unilaterally loyal fans of a particular brand product or service by engaging in the consumer’s aspirational desires through making imaginative associations between actual products and what it is people dream of. However hackers are rather different from fans as they are disruptive entities, sceptical of dominant commercial brands with a desire to create something alternative to the mainstream that fans may typically celebrate.
Lego (the Danish plastic toy brick maker) found that a consumer hacker innovator had broken-into and reprogrammed the software designed for their range of children’s robots toys called Mindstorms NXT. Instead of attempting to prosecute hackers in protection of non-sanctioned usage of proprietary intellectual property and infringement of End User License Agreements (EULA’s), Lego took a non-aggressive stance allowing the hacks to flourish by open-sourcing (releasing to the commons) the NXT firmware along with hardware component schematics and even establishing the LEGO® MINDSTORMS® Developer Program to further promote its product hacking.[10] In so doing, Lego largely embraced end-user hacker innovation and sought ways in which externally created value could be used in order to further enhance the brand image and future innovation strategy, ultimately leading to the sale of more products to consumers that it had not initially targeted in its marketing research. This is a good example of how firm and hacker desires and outcomes can be brought into alignment to allow for mutually beneficial collaboration and to take advantage of each other’s motivations to innovate towards the same ends.
Hackers and firms are in a fundamental epistemological battle of opposing extremes. One the one hand, the necessity for private ownership of property to allow for the appropriation of rents from effort, and on the other, a desire for free and open access to information and property for the benefit of society as a whole. All forms of hacking along the illegal-to-legal dimension demonstrate the application of a common set of underlying ethics that attempt to expand the vectors of communication, culture and knowledge around the World for the betterment of society via the generation and use of ownerless information and resources. Not just restricted to digital programming and software technology development, but also applied to other contexts and domains in the networked, information economy, these ethics form the central belief structure of large groups of consumers who are prepared to partake and contribute time, effort and energy for consumption in the public collective domain.
In this way hacker ethics are a common set of ideological beliefs and values about the relationship between humans and surrounding natural environment that can easily fall in conflict with the commercial interests of firms and the economic legal systems that support the institutions. However if dynamic interconnected relationships can be fully understood, carefully managed and fostered, then internal R&D combined with hacker innovation communities should be closer aligned to make innovation less uncertain in driving market relevant outputs. Potential outcomes of adopting a sympathetic attitude and organisational culture towards hacker ethics in consumer product design may include a higher capacity to facilitate and benefit from unanticipated changes to artefacts through unfiltered contributions from broadly skilled and distributed hacker innovation communities.
True hackers essentially want to learn to control digital devices, rather than be controlled by them. They want to create and improve, not simply nihilistically destroy as may be commonly assumed. Market valuable knowledge and data is constantly being generated and is freely available to be exploited by suitably motivated firms to inform the creation of future product generations and understand unmet needs.
In the next chapter, the dynamics of hacks carried out on technological artefacts will be explored in more detail to understand how modular architectures are affected and innovated upon as a complementary resource for firms.
NEXT: Chapter 4.1 - Hackers, Problem Solving and Innovation
blog comments powered by DisqusPurchase E-Book (ePub & PDF) Version
You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader.
Footnotes
- ↑ Wark, McKenzie. “Information Wants to be Free (But is Everywhere in Chains).” Cultural Studies 20.2-3 (2006).
- ↑ Rosenbaum, R. “Secrets of the Little Blue Box,” Esquire Magazine, October 1971, retrieved November 2012, available at: http://www.historyofphonephreaking.org/docs/rosenbaum1971.pdf
- ↑ Vectoralists control the vectors of information, IP, patents, trademarks; means of producing value by means of war like strategies of communication, command and control.
- ↑ Other ruling classes: pastorialists who control extracting value from land and capitalists who control means of production and distribution of value.
- ↑ With reference to Computer Security Cracking group Anonymous and recent backlash attacks in response to institutions attempting to impose barriers against the public release and sharing of information and knowledge.
- ↑ See film documentary ‘We Are Legion, The Story of the Hacktivists’ (2012) for examples of hacker backlashes against the firm.
- ↑ It is vital to distinguish between Free Software and Open Source. Free Software (GNU Project) refers to the freedom to share code with one’s neighbor for any usage or purpose as a moral argument whilst Open Source provides a business economic argument through code usage being beneficial to the firm but based on strict licensing agreements. Eric Raymond argues that the Free Software term was too wide and ambiguous for business to embrace and instead promoted the Open Source term to be less threatening to existing business models as many software features and designs were appropriated from Microsoft and Unix vendors (HP, IBM & Sun).
- ↑ GNU General Public License v3.0 available at: http://www.gnu.org/copyleft/gpl.html.
- ↑ Reflected in recent firm policy and attitude changes towards Open Source by incumbents such as IBM and Microsoft who now invest and contribute widely into openly developed code.
- ↑ A book titled: LEGO MINDSTORMS NXT Hacker's Guide by Dave Prochnow with the aim of encouraging further exploration of the capabilities of the robotics system for all hacker ages.
References
- [Levy, 1984] ^ Levy, S. (1984). Hackers: Heroes of the Computer Revolution, Penguin.
- [Locke, 1689] ^ Locke, J. (1689). Two Treatises of Government: In the Former, The False Principles and Foundation of Sir Robert Filmer, And His Followers, are Detected and Overthrown. The Latter is an Essay concerning The True Original, Extent, and End of Civil-Government.
- [Smith, 1776] ^ Smith, A. (1776). An Inquiry into the Nature and Causes of the Wealth of Nations. London.
- [Wark, 2004] ^ Wark, M. (2004). A Hacker Manifesto. Cambridge, Harvard College.
- [Marx, 1848] ^ Marx, K. (1848) The Communist Manifesto.
- [Rosenbaum, 1971] ^ Rosenbaum, R. (1971). Secrets of the Little Blue Box. Esquire: 117-226.
- [Parliament, 2000] ^ Parliament, U. (2000). Freedom of Information Act. ch3600s08a. 2000 c. 36.
- [Assange, 2012] ^ Assange, J. (2012). "WikiLeaks." Retrieved Sep, 2012, from http://www.wikileaks.org/.