Difference between revisions of "Product Innovations Designed to be Hacked"
Mikepinder (Talk | contribs) |
Mikepinder (Talk | contribs) |
||
| (4 intermediate revisions by the same user not shown) | |||
| Line 49: | Line 49: | ||
In the case studies discussed so far examples hacker innovation effort and outcomes have been severely disruptive to firms yet in others, entirely complimentary. Future research should focus on defining when and where hacker innovation output is potentially useful and beneficial to firms and under what circumstances. | In the case studies discussed so far examples hacker innovation effort and outcomes have been severely disruptive to firms yet in others, entirely complimentary. Future research should focus on defining when and where hacker innovation output is potentially useful and beneficial to firms and under what circumstances. | ||
| + | === Case Study: Xbox Media Center (XBMC) === | ||
| + | |||
| + | Xbox Media Center (XBMC) is an example of a grass roots hacker innovation that emerged through a desire to unlock hidden module configuration potential within a highly capable proprietary technology: Microsoft’s first generation Xbox games console. | ||
| + | |||
| + | XBMC today is an Open Source media player application developed as a successor to the earlier ''Xbox Media Player'' (XBMP) originally built by two hackers ''d7o3g4q, RUNTiME'' in 2003, designed to run on hardware hacked or modchipped as it is known Xbox game consoles. XBMC allowed hackers to run homebrew games, applications, launch official console games and run emulators for other prior games consoles as well as function as media centre for music, videos, photos and digital content. In 2009 XBMC development for the original Xbox console itself came to an end but continued to mature into a feature-rich media centre, evolving through twelve versions and ported to run on nearly all other computing platforms: PC’s, Linux, OS X, Google Android, Apple TV and iOS platforms. | ||
| + | |||
| + | XBMC emerged from a desire to simply explore the locked-out and untapped potential of a proprietary technology through the circumvention of manufacturer access restrictions to enable creative, innovative and generative exploration to take place. This occurred in direct contravention to Microsoft’s EULAs and future warranty rights and legal frameworks, but also, and in so doing, allowed access to enable the creation of unrestricted features and functionality that were not built in by the profit seeking firm looking to extract rents from its proprietary technology and licensing business model. In essence the act of hacking the Xbox gave users ''agency''. The result was unlocking generativity within a technology of high potential value locked away within its modular design and architecture. XBMC is being continually developed today, running on a broad range of hardware devices such as commercial systems, set-top boxes, Blu-ray and DVD players, other games consoles, embedded computers, SoC (system-on-a-Chip) and televisions. Several firms even sell hardware with XBMC pre-installed such as Pulse-Eight, Xtreamer, ZOTAC, Neuros LINK, BryteWerks and mintBox. | ||
| + | |||
| + | What two inquisitive and determined hackers started (illegally exploring a technology) escalated into a quality proven, industry standard application distributed under the GPL license and provides a significant source of external innovation for all to develop, build-upon, use and enjoy. Arguably the XBMC project influenced the future development of the Xbox 360 console, which put major emphasis on functioning as a home media centre using Microsoft’s own proprietary Windows Media Center application built in. The result of hacker innovation in this instance at least has been to provide vital design trajectory information for the firm when designing its future generation products. | ||
| + | |||
| + | The XBMC project demonstrates how an externally developed innovation built on hacker ethics and mind set can unlock access to hidden modular design parameter configurations and augments systems in new ways outside those perceived by the internal R&D team and ultimately generating new sources of future growth for other firms built on different business models entirely. | ||
| + | |||
| + | == Innovation waves and hacker innovation == | ||
| + | |||
| + | Innovation as a whole can be thought of as a breaking wave in the sea of the market. Truly market-leading innovation design firms exist at the leading edge of the wave crest recurrently anticipating future unknown needs. Innovation followers operate just behind the leading edge producing incremental changes and reproducing variants of market leaders. Hacker innovators operate behind these followers at the trailing edge of the innovation wave. Hacker innovators reconfigure and modify artefacts in external communities as they see fit, whilst removing any access restrictions put in place by the internal R&D firm in the process. | ||
| + | |||
| + | [[File:Hacker-Innovation-Wave.gif|300px|border]] | ||
| + | |||
| + | '''Figure 4. A wave of innovation from leading firms to hacker innovation communities.''' | ||
| + | |||
| + | Internally developed firm-led innovation output is found at the leading edge of the wave crest (Figure 4, indicated by (1)). Hacker innovation generally occurs over longer periods of time within the trailing edge of an innovation wave as a complimentary or disruptive influence to firms (Figure 4, indicated by (3)). Once an innovation enters into the marketplace there is very little a firm can do to prevent the circumvention of measures put in place to fully lock out the exploration of design module configurations held within them.<ref>See earlier examples of entirely failed attempts by firms to lock-out users from modifying their innovations and the consequences of such action. Many firms have now abandoned forms of access restriction to the use, copying and sharing of forms of IP by removing digital rights managements (DRM), copyright restrictions and limiting the number of devices IP can be used upon.</ref> Whilst stereotypically labelled as counterintuitive to commercial firms profit and growth generating strategies, it would be naively dismissive to simply disregard all hacker innovation sources as negatively impacting organisational activities; or at least dismiss them as simply insignificant and unimportant. | ||
| + | |||
| + | Future research should address these issues and provide concrete evidence and theory to help managers and hacker innovation communities alike benefit from each other’s divergent and convergent desires and interests. | ||
| + | |||
| + | This chapter has explored a few examples where such activities are in fact essential and in some cases, dependent upon hacker innovation output for business model success and growth. Figure 5 below summarises the rolling effect of innovation waves and hacker activities, whereby innovations created and developed upon murky legal boundaries (but innovative none the less from external community efforts) feed back into the leading edge of future innovation waves perhaps in other forms or by bolstering and creating new business models entirely in the process (indicated by the red arrow below). | ||
| + | |||
| + | [[File:Hacker-Innovation-Wave-Cycle.gif|400px|border]] | ||
| + | |||
| + | '''Figure 5. Wave rolling effect of innovations made by hackers feeding back into leading innovation output.''' | ||
| + | |||
| + | NEXT: '''Chapter 5.3''' - [[Unlocking Generativity through Hacking]] | ||
| + | |||
| + | <disqus></disqus> | ||
| + | |||
| + | |||
| + | [[File:hackers-and-innovation-epub-pdf-book111.png|250px|link=http://www.mikepinder.co.uk/store/e-books/hackers-innovation-redefinition-examination-outlaw-sources-generativity-future-product-development-strategies/ ]] | ||
| + | |||
| + | <big>'''''Purchase E-Book (ePub & PDF) Version'''''</big> | ||
| + | |||
| + | You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader. | ||
| + | |||
| + | [[File:add-basket-version.png|link=http://www.mikepinder.co.uk/store/e-books/hackers-innovation-redefinition-examination-outlaw-sources-generativity-future-product-development-strategies/]] | ||
Latest revision as of 11:42, 25 April 2016
Contents
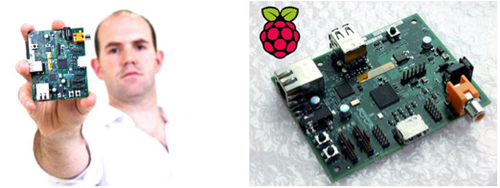
[hide]Case Study: Raspberry Pi
Figure 1. Raspberry Pi – the £22 computer designed to be hacked.
At the absorb and exploit end of the firm-hacker response spectrum is the non- profit UK based Raspberry Pi Foundation who introduced the Raspberry Pi computer in 2012 designed with the sole purpose of being hackable by anyone, of any age and to encourage basic computer science and programming skills in school children.
As reported in the press, the UK IT curriculum merely teaches students how to operate software packages and has been described as “demotivating and dull” by the current Education Secretary Michael Gove as [Joyce, 2012]. Students should be encouraged to learn how to modify, develop and reconfigure software for themselves as they see fit, avoiding the mysterious black box of tricks mind-set. As a consequence it is claimed that lack of coding skills is a significant barrier to future growth and holds back the UK in the digital economy age.[1]
How-to-use or operational skills do not promote a mind set or application of knowledge to make changes, improvements or modifications to existing systems themselves, but merely accept that the way they work is fixed and unchangeable. Operational skills merely allow tasks to be executed according to the pre-existing task structure through algorithms and code designed by a relatively small number of skilled software engineers within firms. These systems lock-out the possibility of further innovation or generative potential, what Zittrain refers to as potential generativity as ‘sterile appliances tethered to a network of control’ [Zittrain, 2008]. Measures put in place to fully control the user experience and maintain quality control, but also and more fervently to protect inter-firm intellectual property and appropriation of rents from within a competitive landscape; not for protecting against un-sanctioned, valued consumer acts of hacking that further-extend an artefacts’ repertoire of task execution possibilities.
One of the founding members of Raspberry Pi recently surmised what he hoped the device would achieve: ‘getting kids to engage creatively with computers: doing interesting things... it doesn’t have to be programming: it can be art [or] design, using computers in a creative way’ [Joyce, 2012]. This also begins to surmise fundamental attributes at the core of the hacker ethics. It mirrors the activities undertaken by firms in the search for new innovation (both radical and incremental) within R&D labs; the main difference being creatively exploring yet-to-be-realised technology configurations to be used in creating new products and services, rather than modifications to existing ones by its users.
Many of today’s digital devices (whether tethered to a network of control or open to modification) have a predefined set of operable functions and tasks inherent in its architecture and limited by its design. Hackers in this sense provide a means and a method to access and contribute to the generative or innovative potential held within a given technology. Whether closed by measures put in place by manufacturers or freely accessible in open systems, hackers will find ways in which to unlock the potential generativity within a technology. There are no true closed systems in the mind of the hacker, only temporary, inconvenient obstacles to overcome (firmware, software and hardware locks, encryption, copy protection, digital rights management and many others) and re- enable open or modifiable devices in the pursuit of executing further tasks with a technology whether deemed legal or otherwise.
The RasPi is an interesting market proposition, built with extremely low barriers to entry due to the £22 price tag and designed with a sole reliance on leveraging hacker communities to enable its future adoption and success. It was initially targeted at Computer Hobbyist and Enthusiast Programmers to build and develop an Open Source software base before educational institutions could begin adopting them in classrooms with a recently pre-built and rich software base.[2] The product launch strategy was intended to leverage hacker ethics, seen as passionate and playful explorers of technology, by selling ten thousand initial units to end users and hacker-innovators ahead of mainstream markets.
The computer is entirely open by design to easily permit the seeking of ways in which to execute new tasks outside those thought possible by the original architects and designers, representing an altogether different strategy to those employed by multinational technology incumbents. The RasPi foundation is trying to actually encourage and generate a culture of hackers, who inquisitively seek to control technology, not be controlled by it.
To innovate on the RasPi, hackers do not need to circumvent barriers, copy protection, encryption standards, locked hardware or bootloaders in order to explore generative and innovative potential. If the Raspberry Pi was designed and manufactured at the same price, with a range of locked-out functionality and features in order to protect various intellectual property rights, hackers would soon find a variety of ways to jailbreak the device, enable further exploration of its generative potential, whether through software or hardware ‘mods’ (as has repeatedly been seen with the proprietary and closed devices using Apple’s iOS).
Users are free to simply operate the device but the main intention is for users to modify it in any way they see fit. Generations of mainstream users have grown used to simply operating desktop PC’s, games consoles, mobile phones and tablets as complex and fragile mystical black boxes with intentional safety locks to prevent untrained users from modifying it via complex and incomprehensible layers of sophisticated code.
Critics of RasPi have commented that children in particular are simply not interested in modifying and creating code, claiming they see devices as simple and dull black boxes akin to washing machines or vacuum cleaners, interested only in the tasks they can achieve, not in how tasks are achieved or modifying the way in which tasks are executed [Rockman, 2012].
This may be true in many cases, but the RasPi represents an experimental, open challenge to hacker and student communities alike both young and old and it remains to be seen exactly how much generativity can be unleashed and its long term influence on future generations of innovators, hackers and entrepreneurs World wide.
Case Study: Black Mesa Source Game Mod
In September 2012 forty computer game mod hacker developers released the eagerly awaited, updated and expanded re-make of a game called Black Mesa Source. It was based on the critically acclaimed first-person-shooter, Half-Life, originally released in 1998 by developers, Valve. After eight years of development the game mod was released for free to the community, designed and built using Valve’s own software develop kit (SDK), to enable hacker-fans to create their own in-game content and mods that could run on the Source engine. Such mods were encouraged by the firm due to the complimentary potential to existing products and further expansion made possible using the existing suite of internally developed games that would in turn generate future rents for the firm.
The project is an example of end-user hackers using toolkits to enable the creation of new and complimentary value from outside organisational boundaries [Piller, 2004] [Piller and Walcher, 2006]. In this instance the purpose of the project was not commercially motivated as the game was released for free. Instead, the motivation came from the technical failings and sub-optimal modular optimisations of an internally developed innovation or port of the original game using the first generation engine to the more advanced second-generation engine named Source. Valve had simply taken the modular design of the older game and ported it to the newer engine without taking full advantage of more advanced rendering technologies made available to the developers in the upgraded engine.[3] At the time, Valve were in the process of developing several of its other leading edge mods using the Source engine and had subsequently chosen to deploy its internal resources in developing these latest generation innovations, instead of allocating them in resurrecting older generation projects to latest technological standards. This typical draw to the most valuable commercial growth driven strategy left an open gap for hacker innovators to fill who felt that Valve had not fully optimised design modules to their most innovative potential and were significantly passionate, skilled and motivated enough to set about deploying resources of their own by entering into software development for themselves.
The result has been a total remake from the ground up (not a simple port) of the original game concept, using similar narrative but with newer models, maps, soundtracks, voice acting and textures in an attempt to create a more immersive in-game world with more complex environments and more challenging gameplay. Many of the features disliked in the narrative of the original game have been improved upon or simply removed and the most enjoyable and engaging parts significantly emphasised. In effect hackers created much higher optimal design modules, more suitable for the market (as they are the market) than those achieved internally by the firm with a tight focus on new innovation output due to its potential financial growth possibilities.
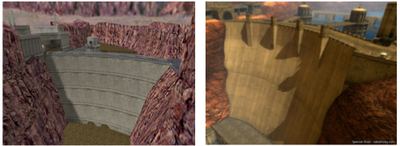
Screenshot examples of Valve’s Half-Life port compared to the hacker created Black Mesa Source Mod:
Figure 2. The Valve game port (left) in comparison to the Black Mesa Source hacker mod (right).
Figure 3. Further example of internally developed game module effort (left) vs. externally developed game mod (right) using the same game developer engine, Source.
The Black Mesa Source project demonstrates how a motivated group of hackers can optimise design modules to a higher quality and execution than those developed internally by the firm (albeit on a much longer time scale, with far fewer resources, number of developers etc.) coordinated by digital, distributed innovation technologies. Where the motivation of the firm is entirely profit driven, gaps of significant unmet need emerge that hacker innovators aim to fill. In this example generativity is entirely complementary (not detrimental) to the wider modular systems design. The complementary output encourages others to purchase other game mods developed commercially for use in the same game engine.
In the case studies discussed so far examples hacker innovation effort and outcomes have been severely disruptive to firms yet in others, entirely complimentary. Future research should focus on defining when and where hacker innovation output is potentially useful and beneficial to firms and under what circumstances.
Case Study: Xbox Media Center (XBMC)
Xbox Media Center (XBMC) is an example of a grass roots hacker innovation that emerged through a desire to unlock hidden module configuration potential within a highly capable proprietary technology: Microsoft’s first generation Xbox games console.
XBMC today is an Open Source media player application developed as a successor to the earlier Xbox Media Player (XBMP) originally built by two hackers d7o3g4q, RUNTiME in 2003, designed to run on hardware hacked or modchipped as it is known Xbox game consoles. XBMC allowed hackers to run homebrew games, applications, launch official console games and run emulators for other prior games consoles as well as function as media centre for music, videos, photos and digital content. In 2009 XBMC development for the original Xbox console itself came to an end but continued to mature into a feature-rich media centre, evolving through twelve versions and ported to run on nearly all other computing platforms: PC’s, Linux, OS X, Google Android, Apple TV and iOS platforms.
XBMC emerged from a desire to simply explore the locked-out and untapped potential of a proprietary technology through the circumvention of manufacturer access restrictions to enable creative, innovative and generative exploration to take place. This occurred in direct contravention to Microsoft’s EULAs and future warranty rights and legal frameworks, but also, and in so doing, allowed access to enable the creation of unrestricted features and functionality that were not built in by the profit seeking firm looking to extract rents from its proprietary technology and licensing business model. In essence the act of hacking the Xbox gave users agency. The result was unlocking generativity within a technology of high potential value locked away within its modular design and architecture. XBMC is being continually developed today, running on a broad range of hardware devices such as commercial systems, set-top boxes, Blu-ray and DVD players, other games consoles, embedded computers, SoC (system-on-a-Chip) and televisions. Several firms even sell hardware with XBMC pre-installed such as Pulse-Eight, Xtreamer, ZOTAC, Neuros LINK, BryteWerks and mintBox.
What two inquisitive and determined hackers started (illegally exploring a technology) escalated into a quality proven, industry standard application distributed under the GPL license and provides a significant source of external innovation for all to develop, build-upon, use and enjoy. Arguably the XBMC project influenced the future development of the Xbox 360 console, which put major emphasis on functioning as a home media centre using Microsoft’s own proprietary Windows Media Center application built in. The result of hacker innovation in this instance at least has been to provide vital design trajectory information for the firm when designing its future generation products.
The XBMC project demonstrates how an externally developed innovation built on hacker ethics and mind set can unlock access to hidden modular design parameter configurations and augments systems in new ways outside those perceived by the internal R&D team and ultimately generating new sources of future growth for other firms built on different business models entirely.
Innovation waves and hacker innovation
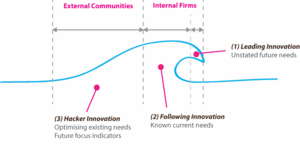
Innovation as a whole can be thought of as a breaking wave in the sea of the market. Truly market-leading innovation design firms exist at the leading edge of the wave crest recurrently anticipating future unknown needs. Innovation followers operate just behind the leading edge producing incremental changes and reproducing variants of market leaders. Hacker innovators operate behind these followers at the trailing edge of the innovation wave. Hacker innovators reconfigure and modify artefacts in external communities as they see fit, whilst removing any access restrictions put in place by the internal R&D firm in the process.
Figure 4. A wave of innovation from leading firms to hacker innovation communities.
Internally developed firm-led innovation output is found at the leading edge of the wave crest (Figure 4, indicated by (1)). Hacker innovation generally occurs over longer periods of time within the trailing edge of an innovation wave as a complimentary or disruptive influence to firms (Figure 4, indicated by (3)). Once an innovation enters into the marketplace there is very little a firm can do to prevent the circumvention of measures put in place to fully lock out the exploration of design module configurations held within them.[4] Whilst stereotypically labelled as counterintuitive to commercial firms profit and growth generating strategies, it would be naively dismissive to simply disregard all hacker innovation sources as negatively impacting organisational activities; or at least dismiss them as simply insignificant and unimportant.
Future research should address these issues and provide concrete evidence and theory to help managers and hacker innovation communities alike benefit from each other’s divergent and convergent desires and interests.
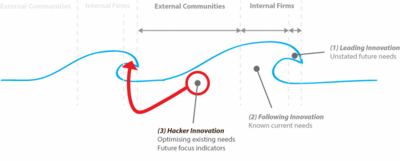
This chapter has explored a few examples where such activities are in fact essential and in some cases, dependent upon hacker innovation output for business model success and growth. Figure 5 below summarises the rolling effect of innovation waves and hacker activities, whereby innovations created and developed upon murky legal boundaries (but innovative none the less from external community efforts) feed back into the leading edge of future innovation waves perhaps in other forms or by bolstering and creating new business models entirely in the process (indicated by the red arrow below).
Figure 5. Wave rolling effect of innovations made by hackers feeding back into leading innovation output.
NEXT: Chapter 5.3 - Unlocking Generativity through Hacking
blog comments powered by DisqusPurchase E-Book (ePub & PDF) Version
You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader.
Footnotes
- Jump up ↑ Google's Eric Schmidt criticises education in the UK (http://www.bbc.co.uk/news/uk-14683133), August 2011).
- Jump up ↑ Raspberry Pi is based on a Broadcom BCM2835 system on a chip (SoC) using ARM architecture chips (commonly used in smartphones) in order to keep per unit prices as low as possible.
- Jump up ↑ New game engine features that were available included vertex and pixel shaders for more realistic water effects; a more advanced Havok physics engine; dynamic light maps; vertex maps, rag dolls and new shadowmap system all using high resolution texture maps.
- Jump up ↑ See earlier examples of entirely failed attempts by firms to lock-out users from modifying their innovations and the consequences of such action. Many firms have now abandoned forms of access restriction to the use, copying and sharing of forms of IP by removing digital rights managements (DRM), copyright restrictions and limiting the number of devices IP can be used upon.
References
- [Joyce, 2012] ^ 1 2 Joyce, J. (2012). "Raspberry Pi computer: Can it get kids into code?". Retrieved April 3, 2012, from http://m.bbc.co.uk/news/technology-17192823.
- [Zittrain, 2008] ^ Zittrain, J. (2008). The Future of the Internet And How to Stop It New Haven & London, Yale University Press.
- [Rockman, 2012] ^ Rockman, S. (2012). "Is raspberry pi a mid-life crisis?". Retrieved April 15, 2012, from http://www.zdnet.co.uk/blogs/fuss-free-phones-simon-rockman-10024919/is-raspberry-pi-a-mid-life-crisis-10025449/.
- [Piller, 2004] ^ Piller, F. N., Franke (2004). "Value Creation by Toolkits for User Innovation and Design - The Case of the Watch Market." Journal of Product Innovation Management 21(6): 401-415.
- [Piller and Walcher, 2006] ^ Piller, F. T. and D. Walcher (2006). "Toolkits for idea competitions: a novel method to integrate users in new product development." R & D Management 36(3): 307-318.
- [Sharma, 2012] Sharma, A. (2012). "Stuxnet - First Cyber Weapon of the World." Retrieved April 11, 2012, from http://www.symantec.com/connect/blogs/stuxnet-first-cyber- weapon-world.
- [Nappenberger, 2012] Nappenberger, B. (2012). We Are Legion: The Story of the Hacktivists.
- [IDEO, 2012] IDEO (2012). "IDEO Labs Bay Area Hack Nights." Retrieved Feb, 2012, from http://labs.ideo.com/2012/03/13/bay-area-hack-night/