Difference between revisions of "Hacker Innovation Cycles"
Mikepinder (Talk | contribs) |
Mikepinder (Talk | contribs) |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 107: | Line 107: | ||
Having outlined how hackers integrate and influence the design of artefact configuration states, in the next chapter ideas and concepts will be developed further to describe examples of actual hacker activities made upon firm innovations within consumer artefacts. | Having outlined how hackers integrate and influence the design of artefact configuration states, in the next chapter ideas and concepts will be developed further to describe examples of actual hacker activities made upon firm innovations within consumer artefacts. | ||
| + | |||
| + | NEXT: '''Chapter 5.1''' - [[Hacker Innovation and Consumer Artefacts]] | ||
| + | |||
| + | <disqus></disqus> | ||
| + | |||
| + | |||
| + | [[File:hackers-and-innovation-epub-pdf-book111.png|250px|link=http://www.mikepinder.co.uk/store/e-books/hackers-innovation-redefinition-examination-outlaw-sources-generativity-future-product-development-strategies/ ]] | ||
| + | |||
| + | <big>'''''Purchase E-Book (ePub & PDF) Version'''''</big> | ||
| + | |||
| + | You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader. | ||
| + | |||
| + | [[File:add-basket-version.png|link=http://www.mikepinder.co.uk/store/e-books/hackers-innovation-redefinition-examination-outlaw-sources-generativity-future-product-development-strategies/]] | ||
| + | |||
== Footnotes == | == Footnotes == | ||
Latest revision as of 10:41, 25 April 2016
Contents
Hacker Innovation Cycles
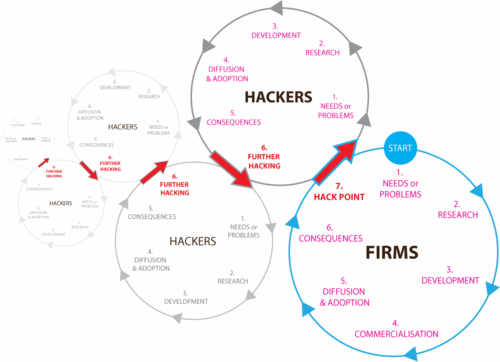
Hacker innovations that are implemented to existing modular products occur after the diffusion and adoption stage of an artefact and exist as a consequence of that very adoption at the ‘hack point’ (Figure 1 below: 7. Hacker innovation cycles and hack point). Hackers find ways in which to break-open closed systems and permit user modifications to take place. Once this is achieved, further needs or problems are established (based on the limits and restrictions of a new and current modular design parameter configuration) and modular operators come into play once again through splitting, substituting, augmenting, excluding, inverting and porting of modules into higher value forms, above those of the original artefact at the start point or from initial point of manufacture and release into the marketplace. The result is a hacker innovation spiral cycle, representing numerous optimal configuration states made freely available to all via digital technologies under the hacker ethics and mind set.
Figure 1. Hacker innovation cycles built upon existing products innovations once design parameter modules are made open and accessible.
As a consequence of the initial adoption of closed system artefacts, hacker innovators see and seek other forms of yet higher value (via further unmet needs, problems, desires or additional features) that a current modular design parameter configuration within an artefact cannot satisfactorily meet.[1] This is achieved at the hack point of the artefacts’ original manufacturer set closed state. Once hacked and made open, the artefact is free to future design configuration changes that allow for further modifications and reconfigurations to take place as hackers see fit. End User License Agreements (EULA’s) and manufacturer warranties will most likely be infringed upon in the process of such pursuits but the desire to innovate is too great to pose a preventative barrier to impassioned hackers. Further intellectual property infringements may occur as hackers seek out higher value or fitness for purpose (in the design evolutionary sense) within the complex modular environment functioning as a complex adaptive system [Fleming, 2001].
The evolution of hacker design is a combination of heuristic (intuitive judgements) and recursion (variation, selection and retention of value held within existing module configurations) as well as problem solving operations, independent of IP regime restrictions and incrementally evolve in each hacker innovation cycle until the module design parameter configuration is in a higher and more valuable configuration state.
These new design parameter configurations may be the result of a significant deployment of resources, time, energy and wealth within hacker communities and form a rich source of new knowledge about optimal module configurations. As original manufacturer configurations can succeed, fail, survive or be eliminated; analysing the resultant re-configured modules from hacker innovation communities would reveal critically important information about lead user needs and problems, relating to higher value peaks, indicative of wider adopter groups (innovators, early adopters, early majority, late majority and laggards). Once obtained and analysed, these data and configurations could be used to indicate a particular design trajectory correlation within a product class, that over time would align the original configurations made by firms with those configurations of hackers communities, resulting in lead user knowledge that could be mapped out onto wider consumer adopter categories and wider markets.
Firm resources are routinely allocated for consumer insight and market research practices in order to reveal unmet needs, desires and expectations. Little comparative de facto research is carried out to understand how consumers hack, tweak, improve or otherwise modify products to more-closely meet their needs or functional expectations (legally or otherwise). This may be due to the expense and legal grey area in which they operate and the difficulties in obtaining primary data from hacker communities, in spite of the openness in which they operate. Firms should understand how collaborative technologies used by hackers influence innovation in the design process once a product or service is out in the marketplace. New sources of value may be generated by hacking acts that could benefit and influence future firm design strategy, management and development.
Examples where this could prove useful are in early design configurations like those found in artefact firmware and systems software are based on limited knowledge of the critical interdependencies, not addressed during the initial design and development process under limited resources. Future manufacturer updates and patches usually address these critical interdependencies as they arise from consumer feedback, complaints and security issues as and when they arrive, but retro-responsive and retroactively. Collaborative Hacker Innovation Networks (or CHINs) provide extensive testing and development environments to find and develop higher design configuration states. CHINs not only provide an additional and potentially complimentary source of innovation to address these unsolved interdependencies, but they also provide design trajectory information through the use of specific module operators that allow for designs to reach their highest value potential possible by extensive experimentation through learning by using, that are not possible within the R&D teams pressed for time amidst tight product development cycles and schedules.
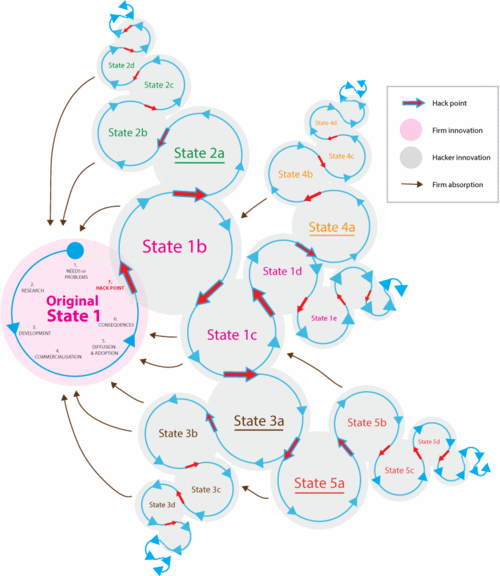
Figure 2, shows a typical design evolution or trajectory spiral based upon the hacking of a firm generated artefact from its original point of manufacture configuration state to different potentially more optimised configuration state. There are a limited number of hacker innovation design iterations until the most optimal design module configuration state is reached, indicated by the decreasing concentric spiral.
Figure 2. Artefact design configuration states once hacked open (hack point) and developed in collaborative hacker innovation networks (COINs) with potential re-absorption by firms.
Extrapolated further, other CHINs involved in design evolutionary spirals are concurrently possible, where other hackers teams decide to take on each other’s module configuration states into different spirals entirely (Figure X, above). The result is a complex, fragmented environment of varying module configuration states, entirely different from those of the original design created by the firm (due to limited time and resource constraints), made possible by opening up access to closed, firm generated, module configurations. This type of arrangement creates fragmentary, messy and dysfunctional innovation platforms as claimed by vertically integrated, walled garden firms. In this instance it is claimed that the market can no longer assure quality, simplicity, relevance and high quality experience.
However if firms were to allocate resources to understand and gain knowledge of and from hacking activities and the ways in which artefact design parameter configurations have been changed, then future product generations could be better informed about the actual market desired design parameters that ought to be included or emphasised upon.
Once an artefact’s modular design is unlocked by hacking it open, there is an explosion of design alternatives (as indicated by artefact states). On strategy for firms faced with this inevitability, is to abandon the search for the best design configuration and settle for a less perfect, cheaper variant, leaving it to hacker innovation communities to invest the time and resources needed to find higher value configurations.[2] In this instance, firms may be relegated to establishing open artefact architectures and interfaces, leaving module level tests, experimentation and higher value seeking configurations to hacker innovators who can more cost-effectively (i.e. at no cost to firms), identify the best combinations for general and wider market consumption.[3] This would amount to a decentralised design evolution process and poses an interesting question as to whether or not designs actually improve and reflect the needs of wider consumer markets, or if simply made worse by poorer performance, instability and ultimately less adoptable.
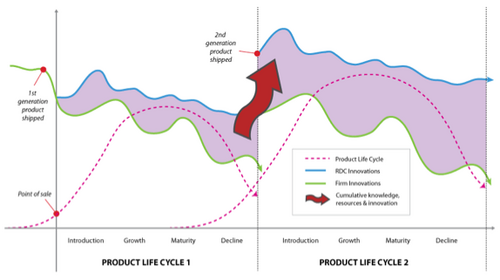
The XDA Developer community provides a fertile primary data research domain in which to answer such questions. Once a manufacturer releases a smartphone handset into the marketplace (based on open and proprietary software), the device is hacked open almost immediately, allowing customised operating systems (firmware, kernels, utilities, ROMs or Read Only Memory) to be installed directly. One example is the HTC Desire HD handset (released in November 2012), which currently has 356 ROM’s under development with 36 guides, 33 mods, 19 fixes, 14 tools and 10 patches available to users.[4] Arguably this provides a rich external development ground for critical interdependencies to be fixed, new features developed, bugs and unnecessary code removed as well as performance and stability improvements made. Firms have the potential to reabsorb modified design configurations to help inform one product lifecycle to he next in a cumulative transfer from one product generation to the next (see Figure 3, below). The difficulty still remains however in developing suitable research methodologies to extract valuable market data vastly distributed among disparate and fluid groups of international developers in a seemingly random, unpredictable and irregular manner, whilst contributing to the common public knowledge pool.
Figure 3. Cumulative knowledge spillovers, resources and innovation potential generated by collaborative hacker innovation networks from one product life cycle to the next.
In order to make innovation less uncertain, the link between producer and user could be made tighter by engaging with hacker activities and extracting data from within collaborative hacker innovation communities. Digital technologies and research methodologies could be developed to trawl activities within hacker communities to help inform design management, design strategy and design trajectory planning and execution for internal firm R&D. If organisations can gauge and understand exactly how consumers are hacking products and in what ways, then logic would follow that future products generations incorporating such modifications within a product class would more closely meet the needs of other adopter categories. Firms could be further informed as to how products can and should be improved upon to meet consumer demand more closely. As an extension of lead users in research by von Hippel et al., firms who learn from users who hack products, post-purchase, rather than lead users who create entirely new products and markets beforehand, have the potential to find a rich and diverse source of incremental, complementary innovation, freely occurring in open digital technology enabled collaborative hacker innovation networks.
When can or cannot firms benefit from hacker innovation?
When hacker innovation occurs to artefacts by extending module configurations across intra firm intellectual property (for example modules are taken from one proprietary technology and integrated into another), firms may not be in a position to directly benefit from such efforts due to the illegality of appropriating value generated from competing firm IP. But when hacker innovation occurs to artefacts within a proprietary or open technology, firms should be in a position to directly benefit as inter-firm intellectual property infringements would not be infringed upon.
Why does hacker innovation occur?
Hacker innovation occurs as a third shift in the locus of innovation. Innovation was understood to initially originate from the individual carrying novelty to the institutionalisation of the firm’s R&D within firms and organisations; and today shifting to concurrent and complimentary innovation occurring within a widely distributed network of hackers using digital technologies [Schumpeter, 1942]. In today’s world, once an internally developed innovation enters the marketplace, it enters into a vast interconnected network of globally distributed and knowledgeable hackers who by sheer desire and passion, see and seek higher forms of artefact value irrespective of institutional limiting frameworks.
Analysing hacker innovation from a musical performance
If the innovating firm were abstractly compared to the dynamics of a musical brass band performance for instance, then several key insights emerge relating to how hacker innovation activities operate in relation to internal firm led innovation. The following scenario describes parallels between a semi professional brass band, its immediate and wider audience outside the venue and the varying sources of innovation for potential influence on the overall value generation within markets.
Abstract analysis of a performance helps reveal and explain the dynamics hacker innovation in relation to traditional internal R&D team efforts in conjunction with those carried out by hackers and end-users from outside firm boundaries. Similarities emerge during such an analysis, drawing parallels to help explain how organisations and hacker communities interact (intentionally or otherwise) as a result of emergent digital technologies and network interconnectivity.
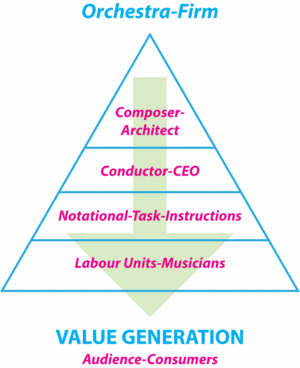
If one were to consider the experienced musicians akin to the individual divisions of tasks and labour via the reading and executing of musical score tasks, then as a whole, represent the firm, under the direction and control of the conductor-CEO. In this sense the orchestra and the firm (orchestra-firm henceforth) behave in not dissimilar ways; with a limited scope of capabilities, resources, experience, tacit knowledge and professional skills comprised by its labour workforce. These capabilities and resources enable its potential cumulative output (greater than the sum of individual persons acting individually), leveraged in order to generate value for the audience-consumers.
The overall quality of outputs generated by the orchestra-firm can be evaluated by differences in independent variables such as: sound range, timing, execution, prior experience, ability to read and play back codified notations from musical scores via instruments, suitability for the audiences’ tastes, number of incorrect notes played for example, amongst many others. These variables provide performance evaluation metrics and can be used to assess the internal capabilities of the orchestra-firm in generating value as assessed in the minds of the audience-consumers.
Knowledge flows
The orchestra consists of individual units of labour or musicians of both sexes and varying ages. Each unit generates a pre-defined acoustic sound wave layer of audible value from codified form by reading, processing and generating musical notes or sound frequencies in a previously defined sequential form from a musical score. Know-how used to execute the musical task comes from prior knowledge and experience through the investment of time, effort and practice to obtain the required level of tacit knowledge needed to successfully complete a musical score in the correct sequence as defined by the composer-architect. Other musicians within the orchestra add further layers of sound value by overlaying yet more complimentary pre-defined musical scores that contribute to the complete piece of music for a concurrent live performance. The goal of this division of labour and effort is the successful execution of the entire music-value score for the consumption by the audience.
Knowledge flow sequence:
- Codified knowledge written in sequential instructions by the composer- architect in a musical score.
- Trained operators decode written sequential instructions from sheet music.
- Instructions are processed in the operators’ minds.
- Commands are sent to the instruments via the musicians’ body.
- Codified acoustic output is generated by instruction processing output by musicians.
- Further layers of codified acoustic output are layered together by the band playing all waves concurrently.
- Cumulative layers of codified sound are transmitted via sound waves to the audience-consumers’ ears.
- Fully layered codified analogue acoustic output is decoded and processed through the senses and in the minds of the audience-consumers.
- Acoustic output is compared to various individual assessment criteria and previous musical experience of other sound performances.
- Assessments are made (using variables previously outlined) in order to make judgments about quality of the value generation effort received.
The multi-layered task is directed and coordinated by the conductor-CEO of the individual labour-musician units according to a master plan or complete musical score that consists of the total sum of all musical value layers required in order to accurately play all labour units as intended by the original composer-architect.
The division of labour within the orchestra-firm conforms to the master plan of codified instructions written-out by the composer-architect delivered by the conductor-CEO and performed by experienced labour unit-musicians or executors of the code. A sum total value proposition is generated by the act of overlaying multiple analogue sound waves uniquely transmitted to the audience for enjoyment, consumption and assessment.
Figure 4. Value generation in orchestra-firms.
Hierarchy plays an important role in the division and management of the value generation task at hand (Figure X). The conductor-CEO brings experience in intimately understanding each labour units’ task division required: what it should sound like, when it should occur, how loud and how fast it should be performed for optimal audience enjoyment. If there were no conductor, it would be almost impossible for the orchestra to self-coordinate and manage its value generation efforts into a tightly structured and well-timed collaborative output for consumption as expected by the audience-consumers.
The role of the orchestra-firm in relation to the audience
Traditionally the consumer consumes the value proposition offered by the orchestra-firm through and at the end of the value chain. In this instance the combinatorial musical division of labour (from around 20 musicians) produced a piece of acoustic value, more complex than the individual musicians could generate independently by themselves. The orchestral task is too complex for an individual musician to execute as a cognitive and physical limitation is reached that can only be surpassed by a division of labour made possible by the stable organisational form of the firm.
Post consumption
After consumption of a piece of music, the audience traditionally follows social etiquette by applauding and demonstrating signs of communal, satisfied consumption: audible appreciation; smiles of faces, clapping hands, whistles, cries for encore for example. The audience-consumer exits the venue as no further value is being generated for consumption. In the era of digital technologies and distributed virtual networks, value generation does not simply end here. It continues outside firm walls and controls, within and by the audience-consumer (or hacker groups) using further knowledge, skills, capabilities and resources.
Digital technologies significantly reduce communication costs between actors within a distributed virtual network allowing for other non-hierarchical forms of organising used to occur and generate further value propositions outside those generated by the firm itself. In light of these technologies, the consumer-audience does not at this point simply consume value in a top-down fashion and leave the music venue once completed and anonymously merging back into the market. Instead, motivated audience members stay behind after the doors are locked or even further, break back into the venue to see and seek-out further unharnessed value.
Imagine the audience did not consist of a hundred loosely connected local villagers, but consisted of tens of millions of virtual, interconnected consumers all acting as unrealised potential labour division nodes and units. An audience on this scale, by proportion is likely to include thousands of other highly-skilled professional musicians, engineers, conductors, architects, sound technicians and other related and interested value generators (hackers) with a keen, passionate interest in musical performances, perhaps with considerably higher resources, capabilities and skills than the current members of the brass band itself. In the traditional loosely connected village audience (consisting of around one hundred members), the likelihood of higher skilled musical performers spectating is significantly less, if any at all.
Now imagine that the musicians left their value generation tools on the stage (instruments, sheet music, stands, lighting, speakers etc.) and returned to their homes. The skilled and unskilled audience members who stayed at the venue can now go enter the stage, pick-up, play, modify, duplicate, replace, destroy and improve the instruments in some form or another as they see fit. Due to interconnected digital technologies and networks the number of consumer hacker-audience members consists several thousand highly skilled, motivated and capable people with the ability to self-coordinate and collaboratively seek out unexploited value peaks within the musical value landscape that the original band members did not and perhaps could not find, as they were outside of the limited capabilities and resources of the small village brass band members.
The audience-consumer-hackers can now get to work. An audience engineer could see that by modifying lights with filters would stop the conductor from perspiring during performances and allow for more confidence whilst conducting, resulting in better musical performances as a whole. A sound technician collaborated with others in placing seat cushion foam on the walls to dramatically decrease echo and increase acoustic sound quality at the venue. A world class composer audience member saw that by changing emphasis of a few notes here and there would greatly add to the dynamic sound quality of performances. A structural engineer saw that by adding tiered flooring for the orchestra performers would allow for an unobstructed view of the conductor to reduce the number of performance errors. A technologist saw a use for a digital device to simultaneously tune all instruments with a single note played into the earpieces of the musicians, enabling the band to quickly tune-up and start performing.
If these audience-consumer-hackers and specialist-spectators had a surplus of resources, time, expertise and experience and were fully prepared to offer hacks back to the band for intrinsic benefits (altruism, peer recognition, self satisfaction, sense of group participation, recruitment potential and for small donations by other audience), then the overall value proposition would be increased at little if any transaction cost.
The sheer number of peer nodes within the distributed, interconnected network that consists the Internet radically multiplies this effect. The potential hackability of an artefact increases with the number of hacker nodes within the network. In this sense the consumer-audience pool increases dramatically by adding further seers and seekers of value who possess excess, deployable resources and capabilities to generate higher value peaks than those realised solely by limited membership of the orchestra-firm itself.
The likely end result is a tighter and higher value proposition more closely aligned with the needs and desires of the consumer-audience. A much higher division of labour is possible with access to a far greater number of potential self-organising hackers, collaborators and value contributors. At this point managing coordination, filtering and selection become critical factors in generating higher value peaks from many individual hacker sources.
The focus in this instance starts to shift towards the increased influence of consumer-audiences upon the design process itself by extending iterations and cycles well into the traditionally static product lifecycle that can inform future design trajectories within product classes. The consumer hacks a path through existing knowledge boundaries, restrictions of established institutions and intellectual property regimes (originally founded by and for the competing firm), by taking control and continuing the development of internally designed artefacts well into a product’s traditional expected lifecycle once in the networks of interconnected hacker-innovators.
Having outlined how hackers integrate and influence the design of artefact configuration states, in the next chapter ideas and concepts will be developed further to describe examples of actual hacker activities made upon firm innovations within consumer artefacts.
NEXT: Chapter 5.1 - Hacker Innovation and Consumer Artefacts
blog comments powered by DisqusPurchase E-Book (ePub & PDF) Version
You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader.
Footnotes
- ↑ The technological limit or capability boundary has not been achieved, therefore is continually searched for.
- ↑ As has been the strategic case with the Raspberry Pi computer (http://www.raspberrypi.org/).
- ↑ This occurred with the failed introduction of the Google Nexus Q, a device that Google claimed was designed to be hackable via a micro USB port. The device was launched with severely limited functionality with the anticipation that hacker innovators would develop additional module configurations, features and functionality outside of the firm. Since initial launch the product has been hacked to run Cyanogen Mod, XBMC (XBOX Media Center), Netflix, Android and turned into a Pong game machine. This marks a different R&D strategy by developing a bare bones systems architecture open to hacking entirely. (Bishop, B. (2012). "Google Nexus Q media streamer: first impressions and video." Retrieved July, 2012, from http://www.theverge.com/2012/6/28/3121991/google-nexus-q-media-streamer-first- impressions.
- ↑ The HTC Desire HD Android Development thread can be accessed on XDA Developers at: http://forum.xda-developers.com/forumdisplay.php?f=765.
References
- [Fleming, 2001] ^ Fleming, L. S., O. (2001). "Technology as a complex adaptive system: evidence from patent data." Research Policy 30: 1019-1039.
- [Schumpeter, 1942] ^ Schumpeter, J. A. (1942). Capitalism, Socialism and Democracy. London, Unwin.