Unlocking Generativity through Hacking
Contents
Unlocking generativity barriers through acts of hacking
As we have seen in several high profile hacker innovation examples, hacking provides an effective means to unlock the inherent generative potential held within the design module configurations within an existing technology through the circumvention of manufacturer established barriers put in place to ensure undisrupted appropriation of rents generated through the creation and exploitation of proprietary and open intellectual property. When acts of hacking break through walled gardens to enable the reconfiguration of design modules, they unlock the inherent generativity potential. Furthermore (and more alarmingly for the value-seeking firm) this situation has the potential to turn a technology into a market disruptor unto itself, its creators and the interests of the commercially motivated firm by preventing it from allowing the flow and generating rents back to the original architect, designer, firm, industry and wider economy. Whilst these forms of hacking may restrict the flow of rents towards the IP owner, they provide new knowledge and innovations to the commons as a whole for the absorptive firm to benefit from.
Case study: OUYA computer games console
Figure 1. OUYA openly hackable computer games console.
Built with an absorb, monitor and influence strategy, OUYA is a yet to launch, openly hackable games console running the Android mobile operating system. The console’s market success depends upon open hacking and generativity of its software and hardware components. It is priced at $99 (under that of all proprietary games consoles from Sony, Microsoft and Nintendo) and all games will operate a free-to-play business model with purchasable add-ons, upgrades, full versions, higher-level access or other in game content.[1] Software will be generated and absorbed from wide variety of external sources such as existing and independent development houses, online distributors (OnLive, Google Play Store) as well as computer hobbyist and enthusiast programmer hackers from indie developers, homebrew communities, open source development and general end users. Other systems software and functionality will stem from existing hacker innovation projects such as Xbox Media Center (XBMC) and Plex Media Center.
In entire contrast to market leading, dominant closed and proprietary consoles, the OUYA’s controller and hardware components have been specifically designed, ‘open to hackers who want to tweak the box and make it their own,’ whilst fitted with standard screws to allow for easy hardware access [OUYA, 2012]. The console is a disruptive innovation in that it will create a new computer games market and value network, initially unprofitable enough for large incumbents to pursue but with the potential to displace earlier (existing) technologies over time. This is evident by open firm strategy actually permitting root hardware and software access, whilst not voiding consumer EULA or warranty; and incorporating a USB port to enable additional peripherals development with test point documentation for printed circuit board (PCB) hacks. The business and innovation strategy is actively and purposefully built upon removing all existing barriers to potential external innovation sources (legal, physical and cultural) to enable full absorption for the firm to grow.
The wider hacker innovation landscape
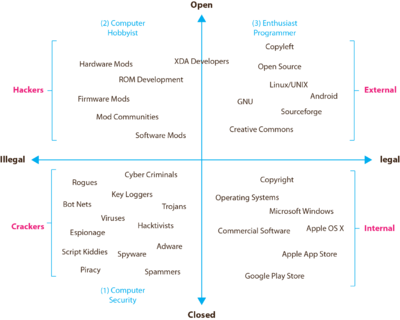
Figure 2 delineates the broad spectrum of hacking acts along two key dimensions: the illegal-to-legal and open-to-closed dimensions and locates them in contrast to internally vs. externally created intellectual property.
Innovation or value creation exists to some degree in all four quadrants and is dependent upon individual, firm or hacker collective motivations and desired outcomes for each party. Common hacker ethics apply broadly across most acts with the exception of internal R&D within firms as highlighted in pink in Figure 2 whose focus is generally in conflict with those of the hacker by creating closed state, hidden information artefacts.
Figure 2. Innovation types along illegal & legal dimensions with hacker innovation.
In quadrant 1 (upper left), hacker innovation and potential sources of generativity are found through the reconfiguring of underlying design modules occurring in various guises to existing firm developed technologies and intellectual property. Complementary and disruptive hacks or modifications built upon internally developed firm innovations via substitution, splitting, augmenting, excluding, inverting or porting of existing firm developed innovations held within technological artefacts.
Quadrant 2 (upper right) represents the heavily researched external or Open Source innovation model and general movement, underpinned by traditional hacker ethics of openness, sharing, collaboration and creative play.
Quadrant 3 (lower left) represents entirely illegal cracker activities (or hacker activities as portrayed in the popular media sense) loosely based upon some hacker ethics, but operates in closed, highly secretive internal teams due to its illegal nature and institutional tracking and surveillance measures.
Quadrant 4 (lower right) represents the traditional firm and internal R&D lab where innovation occurs in teams of employees for firms, based on the generation proprietary intellectual property protected by copyright and patent protection in the pursuit of market domination and innovation leadership.
When viewed in this way, semantic boundaries are revealed to challenge and erode popular conceptions of hacker activities. Entirely illegal, destructive and non-generative acts of hacking (at least from a pro-innovation perspective) still exist and tally up with the popular idea of the hacker. More importantly other forms of hacking are isolated along the illegal-to-legal dimension and provide a niche for new sources of innovation, ideas, design trajectory influencers and more optimal artefact module configuration states that may be useful for future internal R&D innovation development. Also when viewed in this way, significant gaps in the research literature particularly as researchers tend to opt for ‘safe’ areas of phenomenon and interest.
Hacker innovators as general disruptors and generators
Hackers are in essence, disruptors and generators. They are disruptive to firms involved in the pursuit of leading or following intended innovation strategies, whilst generative to consumers and firms involved in improving and optimising artefact module states. Hackers disrupt the established intellectual property regimes used to protect and permit the exclusive appropriation of value from internally developed property for commercial and economic growth within inter-firm rivalry, but not against its hacker-consumers themselves. Disruption is caused by the free and unrestricted reconfiguration and distribution of underlying design modules into new configurations and arrangements, developed from learning by using knowledge, outside the control of the firm through the use of distributed and interconnected digital technologies and spread of widely applicable knowledge and knowhow developed within the Open Source model coupled with the hacker mind set and underlying ethics.
Hackers break down established artefact boundaries and walled gardens by mixing and mashing intellectual property in various forms, porting modules from one artefact to another and/or freely removing and replacing them entirely, whilst optimising use in others. The challenge for firms is firstly to distinguish and recognise the broad typology of hacking activities from those that are illegal to illegal and to identify areas of potentially useful forms of generativity, that could prove vital to future growth strategies (Figure 2 above).
Acts of hacking can transform proprietary firm innovations into disruptive technologies against their creators interests by influencing the patterns of intended social behaviour and modes of consumption in the diffusion, adoption and consumption phases. As well as this, they can provide a rich source of highly optimised and potentially generative sources of new design module configurations (that may be previously unknown or conceived of by the firm) in the trailing edge of an innovation wave initiated and generated internally by the firm. This landscape has the potential to influence future design development trajectories, particularly for proprietary and hybrid-proprietary environments, as design configurations more closely meet the high performing requirements of a market’s lead users and can reflect those of wider adopter categories.
NEXT: Chapter 6.1 - Implications of Hacker Innovation for Firms
blog comments powered by DisqusPurchase E-Book (ePub & PDF) Version
You can read the monograph for free online here or you can purchase an ePub and PDF version for your smartphone, tablet, laptop or desktop e-reader.
Footnotes
- ↑ More info available at http://www.ouya.tv
References
- [OUYA, 2012] ^ OUYA (2012). "A new kind of video game console." Retrieved November, 2012, from http://www.ouya.tv/gamers/.